nifi inovokehttp로 ssl 적용된 https에 접근하는 방법
개방된 네트워크에서는 https에 별다른 설정없이 붙긴 하는 데 사설 인증서를 쓰는 경우 종종 안 붙는 경우가 있어서
정리함
제대로 설정하지 않으면 아래와 같은 error log가 발생함
Yielding processor due to exception encountered as a source processor: javax.net.ssl.SSLHandshakeException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
openssl s_client -connect ip:port 커맨드를 이용해 Server certificate를 가져온다.
테스트는 https://172.30.1.214:8443/nifi/로 진행함(결과값은 www.google.com:443으로 대체)
다음의 작업은 nifi 모든 노드에서 수행되어야함
openssl s_client -connect 172.30.1.214:8443
CONNECTED(00000003)
depth=3 C = BE, O = GlobalSign nv-sa, OU = Root CA, CN = GlobalSign Root CA
verify return:1
depth=2 C = US, O = Google Trust Services LLC, CN = GTS Root R1
verify return:1
depth=1 C = US, O = Google Trust Services LLC, CN = GTS CA 1C3
verify return:1
depth=0 CN = www.google.com
verify return:1
---
Certificate chain
0 s:/CN=www.google.com
i:/C=US/O=Google Trust Services LLC/CN=GTS CA 1C3
1 s:/C=US/O=Google Trust Services LLC/CN=GTS CA 1C3
i:/C=US/O=Google Trust Services LLC/CN=GTS Root R1
2 s:/C=US/O=Google Trust Services LLC/CN=GTS Root R1
i:/C=BE/O=GlobalSign nv-sa/OU=Root CA/CN=GlobalSign Root CA
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIFVTCCBD2gAwIBAgIRAPHFBOn+tB7xCgAAAAE3iiIwDQYJKoZIhvcNAQELBQAw
RjELMAkGA1UEBhMCVVMxIjAgBgNVBAoTGUdvb2dsZSBUcnVzdCBTZXJ2aWNlcyBM
TEMxEzARBgNVBAMTCkdUUyBDQSAxQzMwHhcNMjIwMjE3MTEzMjM1WhcNMjIwNTEy
MTEzMjM0WjAZMRcwFQYDVQQDEw53d3cuZ29vZ2xlLmNvbTCCASIwDQYJKoZIhvcN
AQEBBQADggEPADCCAQoCggEBAKYfeWUR+0+KXTwOAQtpDKHD6mo+eQ7I9xeP7tnF
5DovIZAhO/ll+BFIup2CkHf+D1/qrjJ1kwS9cq8IkBDHi4nVegA/QjsbkZCQd1Zp
jfcjrsD+zeJkKYQJmiyQrmH2yLD3dI8cSkePYttUqKNnFGVMW24ndAou9d4j4ZQ0
Krt5ptYMIeSYQ8XwV6ECNuGqKVCXQVd3R1askmfq2NHFOolKJU2D5eZc01fHQatK
cNBdv5YLv6/m6k3+WEeRak3cufAk90ff82zH608AeCyTcfWSQXXt4JZHzmVFCF3M
im2ZPMvZDxCnbngA5MXw9v9pazuBaAj6mrCIoiWJpzZyUNMCAwEAAaOCAmkwggJl
MA4GA1UdDwEB/wQEAwIFoDATBgNVHSUEDDAKBggrBgEFBQcDATAMBgNVHRMBAf8E
AjAAMB0GA1UdDgQWBBTLATej7iWUNkeiTwbvMrEQ9nBaVzAfBgNVHSMEGDAWgBSK
dH+vhc3ulc09nNDiRhTzcTUdJzBqBggrBgEFBQcBAQReMFwwJwYIKwYBBQUHMAGG
G2h0dHA6Ly9vY3NwLnBraS5nb29nL2d0czFjMzAxBggrBgEFBQcwAoYlaHR0cDov
L3BraS5nb29nL3JlcG8vY2VydHMvZ3RzMWMzLmRlcjAZBgNVHREEEjAQgg53d3cu
Z29vZ2xlLmNvbTAhBgNVHSAEGjAYMAgGBmeBDAECATAMBgorBgEEAdZ5AgUDMDwG
A1UdHwQ1MDMwMaAvoC2GK2h0dHA6Ly9jcmxzLnBraS5nb29nL2d0czFjMy96ZEFU
dDBFeF9Gay5jcmwwggEGBgorBgEEAdZ5AgQCBIH3BIH0APIAdwBGpVXrdfqRIDC1
oolp9PN9ESxBdL79SbiFq/L8cP5tRwAAAX8Hq4ueAAAEAwBIMEYCIQCWvab5kBdQ
hbXQdcPoXO7NS6j99lSkpLjUeDNXC4VOpwIhAP5MlR729yMm7fhToNErTacqeIxQ
e1B/4PhGGdGe/nXCAHcA36Veq2iCTx9sre64X04+WurNohKkal6OOxLAIERcKnMA
AAF/B6uJqwAABAMASDBGAiEA/1+rM33IKm+005txKoHxG+fSsh64BzIsxGssOiHi
UcoCIQC0uOmMBcAhPD2uVIMQHTTS77mFS0/fK2heA20qMvQWETANBgkqhkiG9w0B
AQsFAAOCAQEATHcq0zE3w3B45A1zrgFhgHUtllrk1J/s2vM8O0bq9AbDzO1jYMDD
4nZWsn161Q9v04Aci+OGTOp781fSIPotBIjA7jc41wtbQQzp7TfJRZLTXlJEpBTm
wtQmiKmGVRNCusk/51OJj9jhblk+/lZSapqsLDp6lrHNvtwBsDy4qvIYn0HE2jr+
CkfAwhWqxANNFZfrPjuVDwh+x5cPZasWJ/hrJ98eTUfFAIfyEPdJAD4sIB4p8sYT
zK01yL5OaIzNB432EqxIH9JdTSnjzuMfUQfThLcdnZWf6kpPlodBWWFPg5kjRhr4
YjzkNvI8ypSSt/bNbU7b6f6hcXO2J9+9tQ==
-----END CERTIFICATE-----
subject=/CN=www.google.com
issuer=/C=US/O=Google Trust Services LLC/CN=GTS CA 1C3
---
No client certificate CA names sent
Peer signing digest: SHA256
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 4904 bytes and written 415 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES128-GCM-SHA256
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES128-GCM-SHA256
Session-ID: D416C1B2AF5449385A99883C71BD19C241CA971C6118AC30DD603F4E2E52BDAE
Session-ID-ctx:
Master-Key: 9DC287972EBB492DB431E258248F97AC76A1D8FC18CD98C679BD67096F62A4E2DA1F60EB556B70639EC2652A228B629B
Key-Arg : None
Krb5 Principal: None
PSK identity: None
PSK identity hint: None
TLS session ticket lifetime hint: 100800 (seconds)
TLS session ticket:
0000 - 01 ac ff 47 b6 f1 99 44-ae a6 62 17 e3 75 64 0d ...G...D..b..ud.
0010 - 81 a3 df 58 12 93 0e 0f-21 ae 37 6d bc 8e c6 b1 ...X....!.7m....
0020 - d6 00 66 ff c4 43 f6 25-16 de 86 6e 50 c0 7a 08 ..f..C.%...nP.z.
0030 - 6c 69 b9 55 79 b4 23 8d-44 f7 59 fc fb 99 1b 65 li.Uy.#.D.Y....e
0040 - 63 c0 72 ae f3 fe 74 03-26 64 59 fe 8e af 6c f4 c.r...t.&dY...l.
0050 - e9 6a 32 ae 97 45 08 ce-15 90 82 b8 f9 a2 1a 0c .j2..E..........
0060 - 4c ac 0e 9b 5c fd 8a 61-c0 45 1d 55 45 6e 00 5b L...\..a.E.UEn.[
0070 - 38 cf 2a e7 8b 7d 99 00-33 91 c2 0a 5a 40 d6 3f 8.*..}..3...Z@.?
0080 - 8a 2a 63 4d 6d 74 4e 90-82 0b b9 25 92 81 b8 ee .*cMmtN....%....
0090 - 0c 97 61 8c 07 94 76 72-f1 ff 54 65 8b fb b6 0d ..a...vr..Te....
00a0 - ba ee e9 d7 15 fb d6 4a-15 c5 e3 4c 49 5a 6e fb .......J...LIZn.
00b0 - ae ce 26 cf ac 45 b7 c3-be 37 f1 59 21 87 83 05 ..&..E...7.Y!...
00c0 - 0c b3 4f df 06 c3 c2 33-24 80 b0 9c 53 f7 ce 1f ..O....3$...S...
00d0 - 50 9f 25 5f 65 51 a0 3d-fb f2 67 7b 3b P.%_eQ.=..g{;
Start Time: 1646108019
Timeout : 300 (sec)
Verify return code: 0 (ok)
---
아래 certificate를 test.crt로 저장
vi /tmp/test.crt
| -----BEGIN CERTIFICATE----- MIIFVTCCBD2gAwIBAgIRAPHFBOn+tB7xCgAAAAE3iiIwDQYJKoZIhvcNAQELBQAw RjELMAkGA1UEBhMCVVMxIjAgBgNVBAoTGUdvb2dsZSBUcnVzdCBTZXJ2aWNlcyBM TEMxEzARBgNVBAMTCkdUUyBDQSAxQzMwHhcNMjIwMjE3MTEzMjM1WhcNMjIwNTEy MTEzMjM0WjAZMRcwFQYDVQQDEw53d3cuZ29vZ2xlLmNvbTCCASIwDQYJKoZIhvcN AQEBBQADggEPADCCAQoCggEBAKYfeWUR+0+KXTwOAQtpDKHD6mo+eQ7I9xeP7tnF 5DovIZAhO/ll+BFIup2CkHf+D1/qrjJ1kwS9cq8IkBDHi4nVegA/QjsbkZCQd1Zp jfcjrsD+zeJkKYQJmiyQrmH2yLD3dI8cSkePYttUqKNnFGVMW24ndAou9d4j4ZQ0 Krt5ptYMIeSYQ8XwV6ECNuGqKVCXQVd3R1askmfq2NHFOolKJU2D5eZc01fHQatK cNBdv5YLv6/m6k3+WEeRak3cufAk90ff82zH608AeCyTcfWSQXXt4JZHzmVFCF3M im2ZPMvZDxCnbngA5MXw9v9pazuBaAj6mrCIoiWJpzZyUNMCAwEAAaOCAmkwggJl MA4GA1UdDwEB/wQEAwIFoDATBgNVHSUEDDAKBggrBgEFBQcDATAMBgNVHRMBAf8E AjAAMB0GA1UdDgQWBBTLATej7iWUNkeiTwbvMrEQ9nBaVzAfBgNVHSMEGDAWgBSK dH+vhc3ulc09nNDiRhTzcTUdJzBqBggrBgEFBQcBAQReMFwwJwYIKwYBBQUHMAGG G2h0dHA6Ly9vY3NwLnBraS5nb29nL2d0czFjMzAxBggrBgEFBQcwAoYlaHR0cDov L3BraS5nb29nL3JlcG8vY2VydHMvZ3RzMWMzLmRlcjAZBgNVHREEEjAQgg53d3cu Z29vZ2xlLmNvbTAhBgNVHSAEGjAYMAgGBmeBDAECATAMBgorBgEEAdZ5AgUDMDwG A1UdHwQ1MDMwMaAvoC2GK2h0dHA6Ly9jcmxzLnBraS5nb29nL2d0czFjMy96ZEFU dDBFeF9Gay5jcmwwggEGBgorBgEEAdZ5AgQCBIH3BIH0APIAdwBGpVXrdfqRIDC1 oolp9PN9ESxBdL79SbiFq/L8cP5tRwAAAX8Hq4ueAAAEAwBIMEYCIQCWvab5kBdQ hbXQdcPoXO7NS6j99lSkpLjUeDNXC4VOpwIhAP5MlR729yMm7fhToNErTacqeIxQ e1B/4PhGGdGe/nXCAHcA36Veq2iCTx9sre64X04+WurNohKkal6OOxLAIERcKnMA AAF/B6uJqwAABAMASDBGAiEA/1+rM33IKm+005txKoHxG+fSsh64BzIsxGssOiHi UcoCIQC0uOmMBcAhPD2uVIMQHTTS77mFS0/fK2heA20qMvQWETANBgkqhkiG9w0B AQsFAAOCAQEATHcq0zE3w3B45A1zrgFhgHUtllrk1J/s2vM8O0bq9AbDzO1jYMDD 4nZWsn161Q9v04Aci+OGTOp781fSIPotBIjA7jc41wtbQQzp7TfJRZLTXlJEpBTm wtQmiKmGVRNCusk/51OJj9jhblk+/lZSapqsLDp6lrHNvtwBsDy4qvIYn0HE2jr+ CkfAwhWqxANNFZfrPjuVDwh+x5cPZasWJ/hrJ98eTUfFAIfyEPdJAD4sIB4p8sYT zK01yL5OaIzNB432EqxIH9JdTSnjzuMfUQfThLcdnZWf6kpPlodBWWFPg5kjRhr4 YjzkNvI8ypSSt/bNbU7b6f6hcXO2J9+9tQ== -----END CERTIFICATE----- |
truststore 디렉토리를 만들어줌
mkdir -p /opt/cloudera/security/
truststore 파일을 만들고 인증서를 truststore에 추가하려면 다음의 keytool 명령을 입력
keytool -import -trustcacerts -keystore /opt/cloudera/security/cacerts -storepass changeit -noprompt -alias test -file /tmp/test.crt
Certificate was added to keystore
keytool 명령어로 제대로 들어갔나 확인
default 패스워드는 changeit
alias가 잘 들어가있음
keytool -list -keystore /opt/cloudera/security/cacerts
Enter keystore password:
Keystore type: jks
Keystore provider: SUN
Your keystore contains 1 entry
test, Mar 1, 2022, trustedCertEntry,
Certificate fingerprint (SHA-256): A5:E4:E5:FA:13:75:0D:3C:19:17:8C:79:71:91:A5:C0:4C:BA:3C:A7:1C:4F:6A:9B:89:F9:3C:A7:85:F1:51:7F
인증서를 추가했으니 invokehttp에 config를 채워줌
아래 빨간색으로 체크한 3개를 제외하고 나머지는 모두 default 값

StandardRestrictedSSLContextService configuration은 다음과 같음

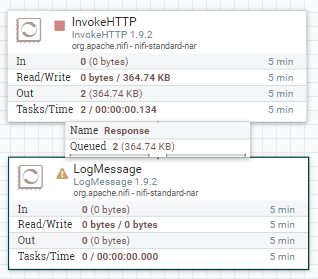
configuration을 다 채우고 run해보면 정상적으로 response가 오는 것을 확인할 수 있다.
참고 : https://docs.oracle.com/cd/E19159-01/820-4605/ablrb/index.html
'NIFI' 카테고리의 다른 글
| cloudera manager에 nifi cfm 2.1.2 서비스 추가하는 방법 (0) | 2022.03.21 |
|---|---|
| nifi updaterecord로 oracle nvl, ms coalesce 함수 사용하기 (0) | 2022.03.04 |
| nifi mergerecord로 여러 개의 flowfile 하나로 병합하기 (0) | 2022.03.02 |
| nifi template (0) | 2022.02.27 |
| NIFI QUEUE MONITORING (use controller service) (0) | 2022.02.26 |



댓글