k8s dashboard를 설치하고 접속해보려고 함.
1. 공식 k8s dashboard yaml파일을 다운받아 apply해준다.
[root@km ~]# kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.4.0/aio/deploy/recommended.yaml
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created
2. dashboard service를 확인한다.
namespace는 kubernetes-dashboard임.
[root@km ~]# kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.107.182.18 <none> 8000/TCP 76s
kubernetes-dashboard ClusterIP 10.107.21.79 <none> 443/TCP 76s
3. 외부 접속을 위해 NodePort 설정
기본으로 TYPE이 ClusterIP로 되어있음.
TYPE을 NodePort로 변경해주고, ports에 nodePort를 추가해준다. nodePort를 추가하지 않으면 랜덤하게 nodePort를
생성하기 때문에 나중에 까먹기 십상임.
[root@km ~]# kubectl edit svc kubernetes-dashboard -n kubernetes-dashboard
# Please edit the object below. Lines beginning with a '#' will be ignored,
# and an empty file will abort the edit. If an error occurs while saving this file will be
# reopened with the relevant failures.
#
apiVersion: v1
kind: Service
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{"apiVersion":"v1","kind":"Service","metadata":{"annotations":{},"labels":{"k8s-app":"kubernetes-dashboard"},"name":"kubernetes-dashboard","namespace":"kubernetes-dashboard"},"spec":{"ports":[{"port":443,"targetPort":8443}],"selector":{"k8s-app":"kubernetes-dashboard"}}}
creationTimestamp: "2022-03-19T19:28:27Z"
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
resourceVersion: "14366"
uid: f3a0f246-90d2-4239-8136-91a16e65cec0
spec:
clusterIP: 10.107.21.79
clusterIPs:
- 10.107.21.79
internalTrafficPolicy: Cluster
ipFamilies:
- IPv4
ipFamilyPolicy: SingleStack
ports: ==> nodePort 추가
- port: 443
protocol: TCP
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
sessionAffinity: None
type: ClusterIP ==> NodePort로 변경
status:
loadBalancer: {}
아래와 같이 수정하고 :wq로 저장한다.
# Please edit the object below. Lines beginning with a '#' will be ignored,
# and an empty file will abort the edit. If an error occurs while saving this file will be
# reopened with the relevant failures.
#
apiVersion: v1
kind: Service
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{"apiVersion":"v1","kind":"Service","metadata":{"annotations":{},"labels":{"k8s-app":"kubernetes-dashboard"},"name":"kubernetes-dashboard","namespace":"kubernetes-dashboard"},"spec":{"ports":[{"port":443,"targetPort":8443}],"selector":{"k8s-app":"kubernetes-dashboard"}}}
creationTimestamp: "2022-03-19T19:28:27Z"
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
resourceVersion: "14747"
uid: f3a0f246-90d2-4239-8136-91a16e65cec0
spec:
clusterIP: 10.107.21.79
clusterIPs:
- 10.107.21.79
externalTrafficPolicy: Cluster
internalTrafficPolicy: Cluster
ipFamilies:
- IPv4
ipFamilyPolicy: SingleStack
ports:
- nodePort: 31000
port: 443
protocol: TCP
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
sessionAffinity: None
type: NodePort
status:
loadBalancer: {}
설정이 정상적으로 변경되면 아래와 같이 service/kubernetes-dashboard edited 나온다.
yaml 포맷을 잘못 맞추면 저장하지 못함.
[root@km ~]# kubectl edit svc kubernetes-dashboard -n kubernetes-dashboard
service/kubernetes-dashboard edited
다시 서비스를 확인해보면 TYPE이 NodePort로 변경되었고, nodePort는 31000으로 설정되있는 것을 확인할 수 있다.
[root@km ~]# kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.107.182.18 <none> 8000/TCP 3m53s
kubernetes-dashboard NodePort 10.107.21.79 <none> 443:31000/TCP 3m53s
이제 chrome에서 master-ip:nodePort로 접속해 dashboard가 잘 올라와있는 지 확인한다.
반드시 http가 아닌 https로 접속해야한다.
내 기준으로는 https://172.30.1.144:31000 임

dashboard WEB UI가 정상적으로 올라왔으니 토큰을 생성해 로그인한다.
일단 default token을 이용해 로그인봤음
Data -> token 값을 복사해 붙여넣고 로그인함.
[root@km ~]# kubectl get secrets
NAME TYPE DATA AGE
default-token-95672 kubernetes.io/service-account-token 3 13h
[root@km ~]# kubectl describe secrets default-token-95672
Name: default-token-95672
Namespace: default
Labels: <none>
Annotations: kubernetes.io/service-account.name: default
kubernetes.io/service-account.uid: 3420fc82-f8f8-43e0-b7c9-a2aa412364a4
Type: kubernetes.io/service-account-token
Data
====
namespace: 7 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6InFpX0w1TzA2SWlkejJDLW9nR0FlQmYzTmdQbFFNYXJKVGRmbDRlZjFaejgifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZmF1bHQtdG9rZW4tOTU2NzIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmYXVsdCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjM0MjBmYzgyLWY4ZjgtNDNlMC1iN2M5LWEyYWE0MTIzNjRhNCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQifQ.pT3YqariJPSA3tdDz_KPGA2uTOx5Bfb4ccub2FIksBczildhejgvkX7GJehSVcBoob1m-5GLjNYhplD-tRslbpTRpVfZq2QNSH7l5ORd2zx-_vCN4Qw6SBSB6_1i6o5oY7M-G22Zt67QXuPArTMnilJXNdv-R9_ZBaGBwn0cO_-8nru4amZGbW7qmGMuassWLNZA_mjsD8obOFbGbSCDdP8ltVJVgg3CkgejMgYy6WR_K3cC-jZdIYeVnptn6qoBHhbHIqnB-9d1RNoys6oB8r8Jh4Sts2oWRV6eydbQJSGlLbphdU5INKC_pjrY75Uubk8v6m6qvnulQB7D5ofsLw
ca.crt: 1099 bytes
4. token 생성
로그인이 되긴 하는 데 이것저것 눌러보니 노드도 안 보이고 다음과 같은 에러가 발생함.
권한 문제가 발생하는 것 같음

그래서 토큰을 직접 생성해서 로그인했음
dashboard-admin.yaml파일 하나 생성해 아래 내용을 적어줬음
kube-system namespace에 ks-admin secret을 생성하는 yaml파일임
name: ks-admin 부분은 변경해서 사용해도 무방하나, namespace는 kube-system으로 고정.
vi dashboard-admin.yaml
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: ks-admin
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: ks-admin
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: ks-admin
namespace: kube-system
yaml 파일을 적용하고 잘 적용되었는 지 확인해본다.
[root@km ~]# kubectl apply -f dashboard-admin.yaml
serviceaccount/ks-admin created
clusterrolebinding.rbac.authorization.k8s.io/admin-user created
[root@km ~]# kubectl get secret -n kube-system | grep ks-admin
ks-admin-token-z89jt kubernetes.io/service-account-token 3 2m37s
생성된 secret을 describe 명령을 통해 보면 token값을 확인할 수 있다.
[root@km ~]# kubectl describe secret ks-admin-token-z89jt -n kube-system
Name: ks-admin-token-z89jt
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: ks-admin
kubernetes.io/service-account.uid: 265d2963-2ef5-4518-a0c8-a90c9dd783e2
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1099 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6InFpX0w1TzA2SWlkejJDLW9nR0FlQmYzTmdQbFFNYXJKVGRmbDRlZjFaejgifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrcy1hZG1pbi10b2tlbi16ODlqdCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrcy1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjI2NWQyOTYzLTJlZjUtNDUxOC1hMGM4LWE5MGM5ZGQ3ODNlMiIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTprcy1hZG1pbiJ9.g4YSHNe3LHO5rqZwksdosaHsSzAtsCwgelkxbYwyYrOKSLcmSJAcsHoJ8SssVe53N-ft6QAcFKAqIBCN_L9Ul4sqfpHlL8SRgNAuNg77T_lW-wLkj65fNV3DWe0tgrLbQuObHBr4gl640O9Ut3pT3RNnMiyW24q_FZcMpcpQQD1yf2c1u-1XFKdKspxdifF1HepOu7SbsaxaQApiYlp5BWTGlGd0KPUpPnXCV21TM_8kBD8BCnoVik6b-GGy-O5-6XMyJpVNwnOQmJtLe91CHnkscEi2gBeLh_YHypL1XHtpaRrNIJYp2WH9YkMUKoGfHWjNDQBNbv760A-ZESNg6A
이제 별다른 에러없이 잘 접속된다.
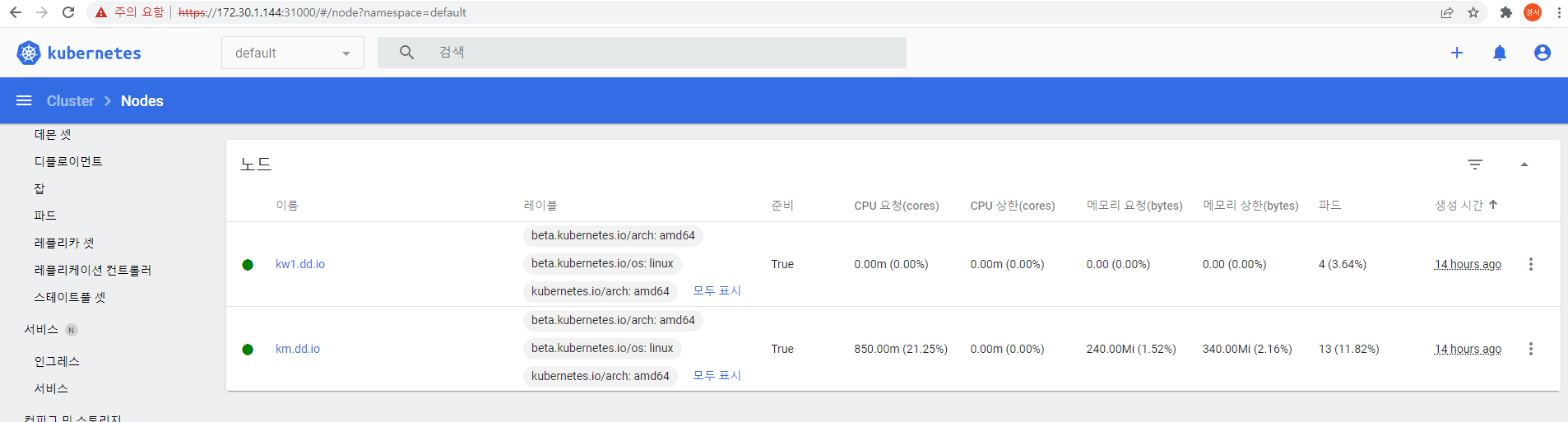
k8s dashboard를 제거하는 방법은 아래와 같음.
[root@km ~]# kubectl delete --all deploy -n kubernetes-dashboard
deployment.apps "dashboard-metrics-scraper" deleted
deployment.apps "kubernetes-dashboard" deleted
[root@km ~]# kubectl delete --all service -n kubernetes-dashboard
service "dashboard-metrics-scraper" deleted
service "kubernetes-dashboard" deleted'kubenetes' 카테고리의 다른 글
| harbor 설치 (2) | 2022.03.21 |
|---|---|
| kubernetes dashboard login skip하는 방법 (0) | 2022.03.20 |
| kubernetes 설치 (0) | 2022.03.19 |
| minikube service web에서 접속하는 방법 (2) | 2022.03.16 |
| minikube dashboard 활성화, 접속 방법 (1) | 2022.03.13 |



댓글